Community
Community support is offered through the mailing lists. You can subscribe to them and ask questions related to PacketFence.
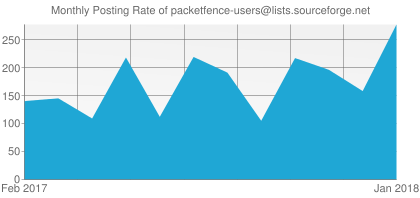
-
Public announcements (new releases, security warnings, etc.)
-
Discussion of PacketFence development
-
User and usage discussions
The PacketFence community is very large and active so do not hesitate to subscribe to the mailing list and ask questions. However, please make sure to respect the following guidelines when posting a new message:
- search for existing answers consult the archives for previously answered questions
- do not hijack threads don't generate a post by replying to somebody else's message and changing the subject and text; newsreader software will see your post as a part of the same thread and mix the two subjects, to everyone's confusion
- send plain text message (no HTML or Rich Text) to avoid getting rejected by the spam filters
- avoid replying to a message on top of the quoted text of the previous correspondence
- be nice you are in effect asking a large group of people to give you some of their time and attention; ensure that your message is relevant to as many of the people receiving the message as possible
New: Community PacketFence Chatbot
Kai Bass, a community member has trained a ChatGPT-based Chatbot to answer common technical questions. Try it here.
Please note that this chatbot is community-driven and is not officially supported by Akamai.
Commercial Support
Network Access Control (NAC) projects are complex in nature because they usually involve many different technologies. We have done hundreds of large-scale deployment projects for prestigious organizations, all around the world. Let us help you make this deployment project a success by using our unmatched expertise!
If you are looking for a PacketFence expert to help you:
- Install, configure, customize and optimize the solution to meet your needs
- Perform a pre or post-implementation audit to make sure your PacketFence deployment performs optimally
- Correct a specific issue with your installation or with components related to it
- Migrate from a previous solution to PacketFence
- Efficiently integrate PacketFence with in-house systems (Active Directory, RADIUS, etc.)
- Develop specific features or add support to new networking equipment
We can help!
Interested in our commercial support services?
Contact UsAvailable Support Package
| Unlimited |
|
|---|---|
| Duration | 1 year |
| Support Method | Support Portal |
| Response Time | 1 hour |
| Support Hours | 24 / 7 |
| Multi-Server | No |
| Notifications | Security / Bug Fixes |
| Bug Fixes | Yes |
| Included Incidents | Unlimited |
| Cost | $5,000 USD per PacketFence server |
| Order |
Supported operating systems are:
- Red Hat Enterprise Linux (RHEL) 8
- Debian 12
The support packages do not include:
- components installation
- custom development
- preventive system monitoring
- training and documentation
Documentation
| Installation Guide | Download PDF Read Online |
| Upgrade Guide | Download PDF Read Online |
| Network Devices Configuration Guide | Download PDF Read Online |
| Clustering Quick Installation Guide | Download PDF Read Online |
| Developer's Guide | Download PDF Read Online |
| OpenApi Specification - REST API (Stable) | Read Online |
| OpenApi Specification - REST API (Development) | Read Online |
| OpenApi Specification - REST API (Per Release) | v13.0 |
FAQ
Restrict communications in Registration/Isolation VLANs
This article is only relevant if you are using Cisco Switches with VLAN access map capabilities.
One downside of the isolation and registration VLAN is that they are usually flat (not routed VLANs) with a lot of people in them. Furthermore, in the isolation VLAN, it can became a real “battle” zone where users are seeing each other and can be infected by viruses or malware from others.
In order to mitigate that problem, you can create VLAN access map on the access switches. You can then drop any traffic that does not go or come from the PacketFence registration/isolation interface. Here is a quick example how to achieve that in the isolation VLAN.
First, create your ACL to match the traffic:
ip access-list extended pf-isol
permit ip host pf_host any
permit icmp any host pf_host
permit tcp any host pf_host eq www
permit tcp any host pf_host eq 443
permit udp any host pf_host eq domain
permit udp any host 255.255.255.255 eq bootps
permit udp any host pf_host eq bootps
Secondly, apply the VLAN map:
vlan access-map Isolation 10
action forward
match ip address pf-isol
vlan filter Isolation vlan-list ISOLATION_VLANID
Bugs
If you encounter a possible bug with PacketFence, you can access our github page.
Please make sure to respect the following guidelines when reporting a bug:
- verify that the bug you found is not already known or even fixed in the trunk version
- make the actual facts very clear; be precise, we need to be able to reproduce the problem
- explain your speculations, if any
- add a screenshot to the ticket if appropriate

